Contents of Articles:
- Introduction
- TCP/IP Basics
- TCP/IP layer model
- Why Ports Matter and the Meaning of the Term 'Socket'
- What is DNS and What is used for?
- Protocol Stack, Link Layer again
- Point-to-Point Protocols
- Conclusion
Introduction
The TCP/IP protocol stack is widely used. It is used as the basis for the global Internet. Let's consider the stack’s basic concepts and features.
TCP/IP Basics
The TCP/IP protocol stack is a network model that describes the process of transmitting digital data. It is named after two main protocols; the model is used for the modern Internet. It seems incredible now, but in the 70s information could not be transferred from one network to another. The Internet protocol stack known as TCP/IP provides this capability.
The network model was created in the US Department of Defense, so the TCP/IP model is sometimes called the DoD. People who know the OSI model could understand the construction of the TCP/IP faster because both models are divided into layers. Every layer has an internal protocol with a number of features.
So, TCP/IP is a reliable and connection-oriented protocol suite. It connects the two devices to deliver data correctly and without any errors. This accuracy is achieved through the use of various mechanisms such as acknowledgment packets, retransmission of lost or corrupted packets, and flow control.
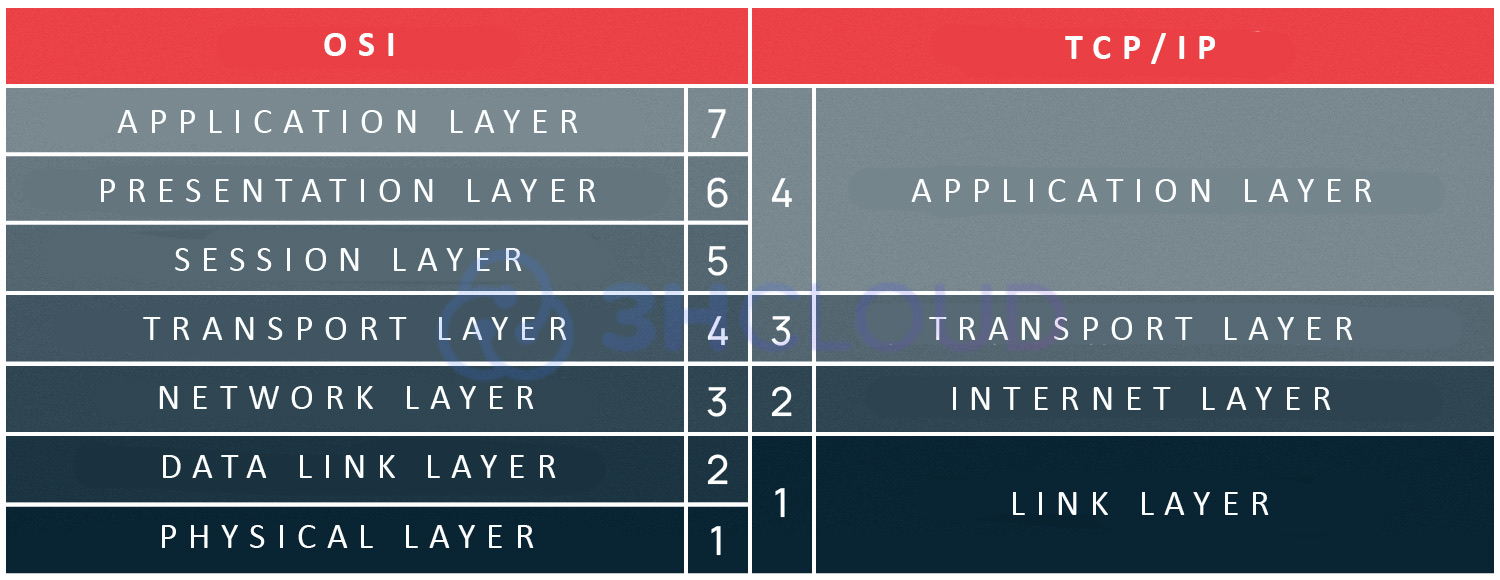
TCP/IP layer model
Above, we have already mentioned that the TCP/IP model is divided into layers, just like OSI. However, the difference between the two models lies in the number of layers. The documents defining the certification of the model are RFC 1122 and RFC 1123. These standards describe the four levels of abstraction in the TCP/IP model: the application, transport, internet, and link layers.
There are other versions of the model description, including those that include a different number of levels and their names. However, we stick to the original version and will continue to consider the four levels of the model in this article.
Link Layer
Information is exchanged between network devices at the link layer. The key goal of every layer is to work with the data in a correct way, each having its specific tasks, to transmit it to another device. This process determines the quality of information transfer at the link layer. The data is encoded, separated into individual packets, and transmitted along the intended channel, which is a transmission medium.
This layer also calculates the maximum distance for packets’ transmission, signal frequency, response delay, etc. These are physical properties that concern the data delivery. Usually, it is necessary to use Ethernet.
Internet Layer
The Internet includes many local networks that interact with each other. The internetwork layer is used to describe the provision of interaction among local networks.
Internetworking, which involves the integration of local networks into a global one, is the core principle of the Internet. Local networks around the world are united into a global one, and data transfer between these networks is carried out by backbone and edge routers.
It is at the internetwork level that the IP protocol operates, which makes it possible to unite different networks into a global one. Similar to the TCP protocol, it gave the name to the model discussed in this article.
Subnet Mask And IP Addresses
Subnet masking provides a means for the router to determine the packet location, and when it is true, it indicates how the packet will be sent. Any network that has its own protocols and uses subnet masking can be classified as a subnet. If the subnets of the sender and receiver differ, the packet is forwarded to the second router, then to the third, and so forth, until it reaches the destination.
The router uses IP to find the recipient. Each network device has its unique IP address, and in the global network, two devices cannot have the same IP address.
IPv4 is a protocol which was created in 1981. It assigns to each device a 32-bit IP address, which limits the maximum possible number of unique addresses to 4 billion (2^32). It consists of four blocks (octets) of numbers from 0 to 255, separated by three dots.The first octet of an IP address indicates the network class, of which there are five: A, B, C, D, and E. Addresses in class D are reserved for multicast, and class E addresses are not used.
Due to the rapid growth of the Internet, there was an urgent need to increase the number of possible IP addresses. In 1995, the IPv6 protocol (IP version 6, version 6) was introduced. It uses 128-bit addresses and enables unique addresses to be assigned to 2^128 devices.
IPv6 takes the form of eight blocks of four hexadecimal values, with each block separated by a colon.
IPv6 addresses are long, and they are allowed to be shortened according to certain rules, which are also described by the RFC:
- to write the address, lowercase letters of the Latin alphabet are used;
- leading zeros may be omitted;
- groups of zeros in a row can also be shortened and replaced with a double colon.
IP is designed to identify the recipient and deliver information to them.It provides a service for higher-level protocols but does not guarantee the integrity of the delivered information.
IP is capable of encapsulating other protocols, providing a space where they can be embedded. Examples of such protocols include ICMP (Internet Control Message Protocol) and IGMP (Internet Group Management Protocol). Information about the encapsulated protocol is reflected in the IP packet header. Thus, ICMP is designated by the number 1, and IGMP is designated by the number 2.
ICMP
ICMP is used for various purposes, including error reporting, network troubleshooting, and ping requests.
ICMP reports on the unavailability of devices on the network are transmitted when devices are unreachable. Moreover, ICMP is used in network diagnostics.
ICMP does not transmit any data, which distinguishes it from transport layer protocols such as TCP and UDP. It is similar to IP and operates at the internetwork layer. Basically, it is actually an integral part of the implementation of the TCP/IP model. It's worth noting that different versions of IP also use different versions of the ICMP protocol.

Transport Layer
The TCP and UDP protocols are necessary for the correct data delivery to ensure proper communication with other devices.
TCP is reliable, it ensures the transfer of information by checking whether it has arrived, how complete the amount of information received is, etc. TCP allows two end devices to exchange packets over an established connection. TCP ensures that the correct order of the received and assembled information is maintained by ensuring that it is received and assembled correctly.
UDP is unreliable and deals with the transmission of autonomous datagrams. UDP does not guarantee that all datagrams will reach the recipient. Datagrams already contain all the necessary information to reach the recipient, but they may still be lost or delivered in a different order than when sent.
UDP is not typically used if reliable information transfer is required. It makes sense to use UDP where the loss of some information is not critical for the application, for example, in video games or video streaming. UDP is needed when making a repeated request is difficult or unjustified for some reason.
Transport layer protocols do not interpret information received from upper or lower layers, they only serve as a transmission channel, but there are exceptions. RSVP (Resource ReSerVation Protocol) can be used, for example, by routers or firewalls to analyze traffic and decide whether to transmit or reject it depending on the content.
Application Layer
TCP/IP utilizes the TCP/IP protocol's intermediate layers as there is no need for additional layers to achieve the same level of abstraction. Libraries and application programming interfaces (APIs) provide data formatting and presentation functions, while UI and Scaling are used to control data format and presentation functions. They are similar to knowledge bases that contain information about the interactions between applications, similar to a knowledge base. In response to a library or API being used by services or applications, they provide a list of necessary actions and detailed guidelines for carrying them out when requested to complete the task.
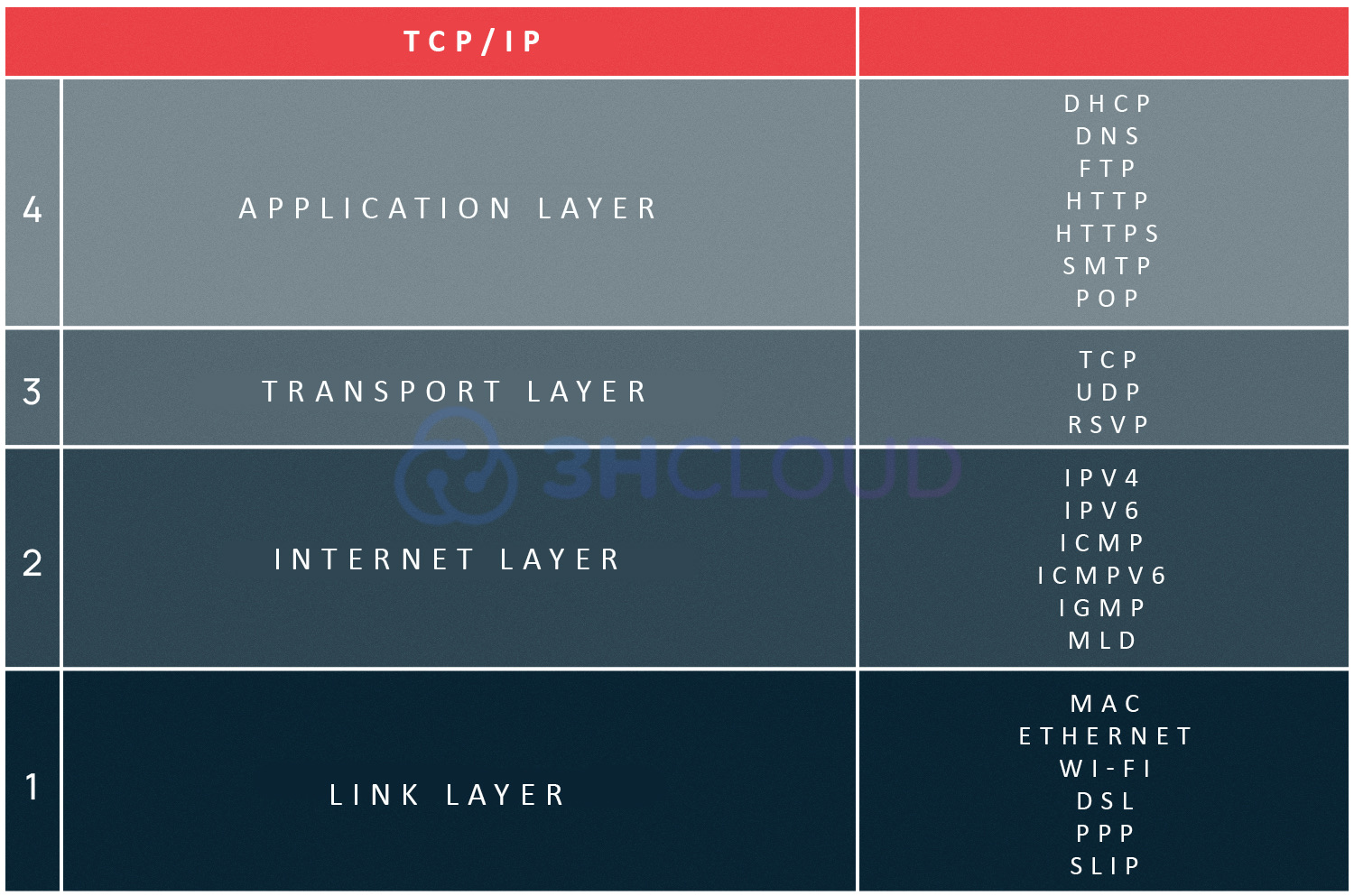
The application layer protocol in most apps provides services to users or lower layers, which are integrated into the system to provide shared services over pre-existing connections. Protocols are distinct protocols for most applications. For instance, HTTP is used by browsers to send hypertext over the network, SMTP is used by email clients to transfer mail, FTP is used by FTP clients to transfer files, and DHCP services use the DHCP IP address assignment protocol, and so on.
Why Ports Matter and the Meaning of the Term 'Socket'
Apps at the application level communicate with the previous layer, the transport layer, but they see its Internet protocols as “black boxes”. To receive and transmit information, they can work, for example, with TCP or UDP, but they only understand the final address in the form of IP and port, but not the principle of their operation.
As mentioned earlier, an IP address is assigned to each end device by the network layer protocol. But data exchange occurs not between end devices, but between applications installed on them. Just an IP address is not enough to gain access to a particular network application. So, ports are also used to identify apps. The combination of an IP address and port is called a socket.
In addition to their own protocols, programs at the application level often have a fixed port number for accessing the network. The Internet Assigned Numbers Authority (IANA), which allocates IP address ranges, is also responsible for assigning ports to network applications.
Thus, email apps that communicate via the SMTP protocol use port 25, when using the POP3 protocol - port 110. A port is always written after the IP address and is separated from it by a colon; for example, 192.168.0.1:443.
What is DNS and What is used for?
DNS was created so as not to remember the numeric addresses of Internet servers. DNS always listens on port 53 and resolves alphabetic network domain names to numeric IP addresses and vice versa. It allows you to not remember the IP - the computer itself sends the request to port 53 of the DNS server obtained from the Internet service provider.
The DNS server gives the computer the answer. Then, the computer establishes a connection to the web server of the received IP, which listens on port 80 for the HTTP protocol and on port 443 for HTTPS. The port is not displayed in the address bar, but is used by default.
Network models use a special method (encapsulation) to ensure the correct operation of protocols at various levels. The essence of this method is to add the current layer protocol header to the data received from the higher layer protocol. The reverse process described is called decapsulation. Both processes are carried out on the computers of the recipient and sender of the data alternately, thus allowing one side of the channel not to be kept busy for a long time, leaving time to transfer information to the other computer.
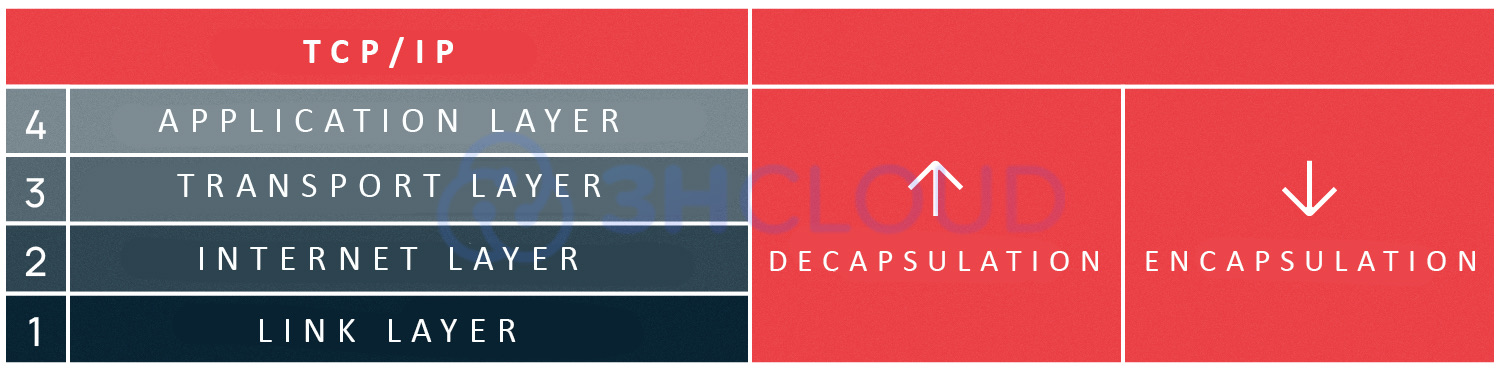
Protocol Stack, Link Layer again
Let's talk about the link layer of the TCP/IP model. So, it’s necessary to know what a stack is.
Most users know the Ethernet protocol. According to the Ethernet standard, each sender and destination device has a specific MAC address. They are the hardware identifier. The MAC address is encapsulated in Ethernet along with the type of data transmission and the data itself. A piece of data constructed in accordance with Ethernet is called a frame.
The MAC address of each device is unique, and two hardware devices with the same address may not exist. A match may cause network problems. Thus, when a frame is received, the network adapter is involved in extracting the received information and processing it further.
After familiarizing yourself with the level structure of the model, it becomes clear that information cannot be transferred directly between two computers. First, the frames are transmitted to the internetwork layer, where a unique IP is assigned to the sender's computer and the recipient's computer. Then, the information transmission occurs at the transport layer in the form of TCP frames or UDP datagrams.
Service information is added to the existing information at each stage. The addition of service information to the main one is provided by different protocols in the following way:
- Ethernet;
- TCP;
- a port, meaning an application with a protocol delegated.
This nesting is called a protocol stack, named TCP/IP after the two main protocols of the model.
Point-to-Point Protocols
Let's talk about the Point-to-Point protocol, also known as PPP. PPP is unique in its functions; it is used for communication between two routers without any involvement of a host or any network infrastructure in between. It also supplies authentication, encryption, and data compression. It is commonly used in the construction of physical networks.
PPP has two subtypes - PPPoE (PPP over Ethernet) and PPPoA (PPP over asynchronous data transfer method - ATM), Internet providers often use them for DSL connections.
PPP and its older analog SLIP (Serial Internet Protocol) formally belong to the TCP/IP internetwork layer, but they are sometimes classified as a separate category. The advantage of PPP is that it does not require network infrastructure to connect and eliminates the need for routers. These factors determine the specifics of using PPP protocols.
Conclusion
The TCP/IP stack regulates the interaction of different layers. The key concept here is protocols, which form a stack by building upon each other to transfer data. The considered model has a simplified architecture compared to OSI.
The model itself remains unchanged, while protocol standards can be updated, making TCP/IP even easier to work with. The TCP/IP stack became widespread and was used first as the basis for creating a global network due to all its advantages, and later to make a stable Internet.















